| Home | Trees | Indices | Help |
|
|---|
|
|

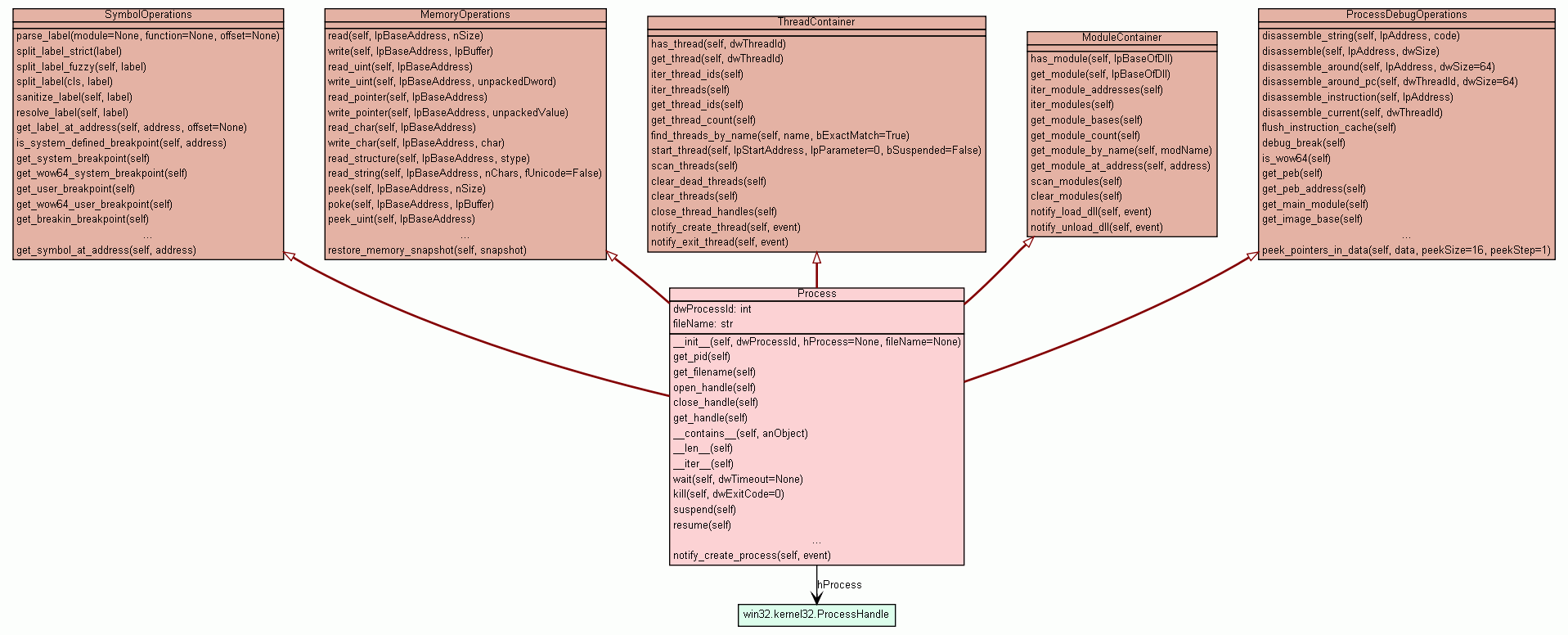
Interface to a process. Contains threads and modules snapshots.
|
|||
|
__ThreadsAndModulesIterator Iterator object for Process objects. |
|||
|
|||
|
|||
| list of Window |
|
||
|
|||
| str |
|
||
| dict( int → str ) |
|
||
| int or None |
|
||
| int or None |
|
||
| int or None |
|
||
| str, unicode |
|
||
|
|||
| list( win32.MemoryBasicInformation ) |
|
||
|
Inherited from |
|||
| Properties | |||
|---|---|---|---|
| int |
|
||
| str |
|
||
| bool |
|
||
| bool |
|
||
| int |
|
||
| int |
|
||
| int |
|
||
| Module |
|
||
| win32.PEB |
|
||
| int |
|
||
| bool |
|
||
| Instrumentation | |||
|
|||
|
|||
|
|||
|
|||
| tuple( Thread, int ) |
|
||
|
|||
|
|||
| Processes snapshot | |||
| bool |
|
||
| int |
|
||
| iterator |
|
||
|
|||
|
|||
| Handle | |||
|
|||
|
|||
| ProcessHandle |
|
||
| Memory mapping | |||
| bool |
|
||
| list( win32.MemoryBasicInformation ) |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| bool |
|
||
| int |
|
||
| int |
|
||
| win32.MemoryBasicInformation |
|
||
| Memory read | |||
| str |
|
||
| int |
|
||
| int |
|
||
| str, unicode |
|
||
| int |
|
||
| str |
|
||
| int |
|
||
| int |
|
||
| int |
|
||
| int |
|
||
| Memory write | |||
| int |
|
||
| int |
|
||
| int |
|
||
| int |
|
||
|
|||
|
|||
|
|||
|
|||
| Disassembly | |||
| list of tuple( long, int, str, str ) |
|
||
| list of tuple( long, int, str, str ) |
|
||
| list of tuple( long, int, str, str ) |
|
||
| tuple( long, int, str, str ) |
|
||
| tuple( long, int, str, str ) |
|
||
| list of tuple( long, int, str, str ) |
|
||
| Debugging | |||
|
|||
|
|||
| int or None |
|
||
| int or None |
|
||
| int or None |
|
||
| bool |
|
||
| dict( str → str ) |
|
||
| Labels | |||
| str |
|
||
| int |
|
||
| str |
|
||
| tuple( str or None, str or int or None, int or None ) |
|
||
| Symbols | |||
|
|||
|
|||
|
|||
|
|||
|
|||
|
|||
| Threads snapshot | |||
|
|||
|
|||
|
|||
| list( Thread ) |
|
||
| Thread |
|
||
| int |
|
||
| list( int ) |
|
||
| bool |
|
||
| dictionary-keyiterator |
|
||
| dictionary-valueiterator |
|
||
|
|||
| Event notifications (private) | |||
|
|||
|
|||
|
|||
|
|||
|
|||
| Modules snapshot | |||
|
|||
| Module |
|
||
| Module |
|
||
| list( int... ) |
|
||
| Module |
|
||
| int |
|
||
| bool |
|
||
| dictionary-keyiterator |
|
||
| dictionary-valueiterator |
|
||
|
|||
|
|||
| Labels | |||
|---|---|---|---|
| tuple( str or None, str or int or None, int or None ) |
|
||
|
|||
| Labels | |||
|---|---|---|---|
| str |
|
||
| tuple( str or None, str or int or None, int or None ) |
|
||
|
|||
| int |
dwProcessId Global process ID. |
||
| str |
fileName Filename of the main module. |
||
| ProcessHandle |
hProcess Handle to the process. |
||
|
|||
|
Inherited from |
|||
|
|||
x.__init__(...) initializes x; see x.__class__.__doc__ for signature
|
|
|
|
The same as:
|
See Also: get_thread_count, get_module_count |
See Also: iter_threads, iter_modules |
Waits for the process to finish executing.
|
Terminates the execution of the process.
|
Suspends execution on all threads of the process.
|
Resumes execution on all threads of the process.
|
Tries to determine if the process is being debugged by another process. It may detect other debuggers besides WinAppDbg.
Warning: May return inaccurate results when some anti-debug techniques are used by the target process. Note: To know if a process currently being debugged by a Debug object, call Debug.is_debugee instead. |
|
Warning:
If a process returns |
|
Injects relocatable code into the process memory and executes it.
See Also: inject_dll |
Injects a DLL into the process memory.
Warning:
Setting See Also: inject_code |
Injects a new thread to call ExitProcess(). Optionally waits for the injected thread to finish.
Warning:
Setting |
Notify the creation of a new process. This is done automatically by the Debug class, you shouldn't need to call it yourself.
|
|
|||
dwProcessIdGlobal process ID. Use get_pid instead.
|
fileNameFilename of the main module. Use get_filename instead.
|
hProcessHandle to the process. Use get_handle instead.
|
| Home | Trees | Indices | Help |
|
|---|
| Generated by Epydoc 3.0.1 on Fri Feb 12 19:46:23 2010 | http://epydoc.sourceforge.net |