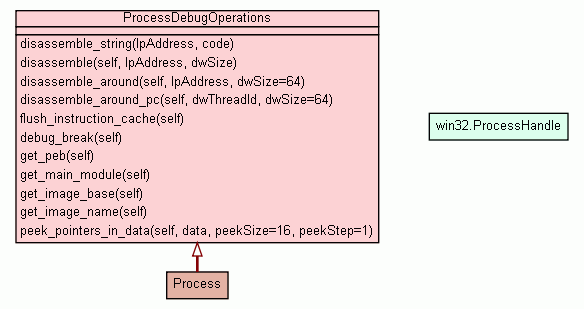
Encapsulates several useful debugging routines for processes.
|
Inherited from object:
__delattr__,
__getattribute__,
__hash__,
__init__,
__new__,
__reduce__,
__reduce_ex__,
__repr__,
__setattr__,
__str__
|
|
PEB
|
get_peb(self)
Returns a copy of the PEB. |
|
|
|
Module
|
|
|
int
|
get_image_base(self)
Returns:
Image base address for the process main module. |
|
|
|
int
|
|
|
list of tuple( long, int, str, str )
|
disassemble(self,
lpAddress,
dwSize)
Disassemble instructions from the address space of the process. |
|
|
|
list of tuple( long, int, str, str )
|
|
|
list of tuple( long, int, str, str )
|
disassemble_around_pc(self,
dwThreadId,
dwSize=64)
Disassemble around the program counter of the given thread. |
|
|
|
|
|
|
|
debug_break(self)
Triggers the system breakpoint in the process. |
|
|
|
dict( str → str )
|
peek_pointers_in_data(self,
data,
peekSize=16,
peekStep=1)
Tries to guess which values in the given data are valid pointers, and
reads some data from them. |
|
|